In today’s enterprise environments, securing directory services is a critical step in protecting authentication data and sensitive organizational information. By default, LDAP (Lightweight Directory Access Protocol) communication occurs in clear text over port 389, which exposes user credentials and directory queries to potential interception.
To mitigate this risk, Microsoft recommends configuring LDAPS (LDAP over SSL/TLS), which encrypts communication between clients and domain controllers. In this post, we’ll walk through how to enable LDAPS on a Windows Server Domain Controller, restrict plain LDAP bindings, and enable event logging to monitor LDAP traffic.
🧠 What Is LDAPS?
LDAPS (LDAP over SSL/TLS) is the secure version of the LDAP protocol.
- LDAP (port 389): Transmits data in plain text.
- LDAPS (port 636): Encrypts data using SSL/TLS certificates.
Using LDAPS ensures that authentication credentials, directory queries, and responses are encrypted, preventing eavesdropping or tampering.
⚙️ Step-by-Step: Enabling LDAPS on a Domain Controller
1. Obtain or Create a Certificate for LDAPS
LDAPS requires a valid SSL/TLS certificate installed on each domain controller.
Requirements:
- The certificate must include:
- Server Authentication (1.3.6.1.5.5.7.3.1) in the Enhanced Key Usage (EKU)
- The FQDN of the domain controller in the Subject or Subject Alternative Name (SAN) field.
- Issued by a trusted Certificate Authority (CA) (internal or public).
To request a certificate:
- Open Certificates (Local Computer) MMC snap-in.
- Navigate to Personal → Certificates.
- Right-click → All Tasks → Request New Certificate.
- Select a template supporting Server Authentication.
- Submit and install.
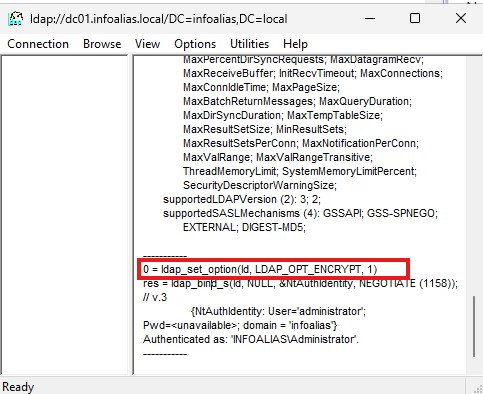
2. Verify LDAPS is Working
Once installed, restart the Active Directory Domain Services (NTDS) or reboot the DC.
✅ Test with Ldp.exe
- Open Ldp.exe (included with RSAT tools).
- Click Connection → Connect.
- Enter the DC’s FQDN, port 636, and check SSL.
- Click OK.
- A successful bind confirms LDAPS is active.
✅ Test with PowerShell
Test-NetConnection -ComputerName <DC-FQDN> -Port 636
A successful connection confirms LDAPS is listening.
3. Restrict Plain LDAP Binding
Once LDAPS is verified, you can restrict unencrypted LDAP binds to enforce secure communication.
🔒 Option 1: Using Group Policy
- Open Group Policy Management Console (GPMC).
- Edit Default Domain Controllers Policy.
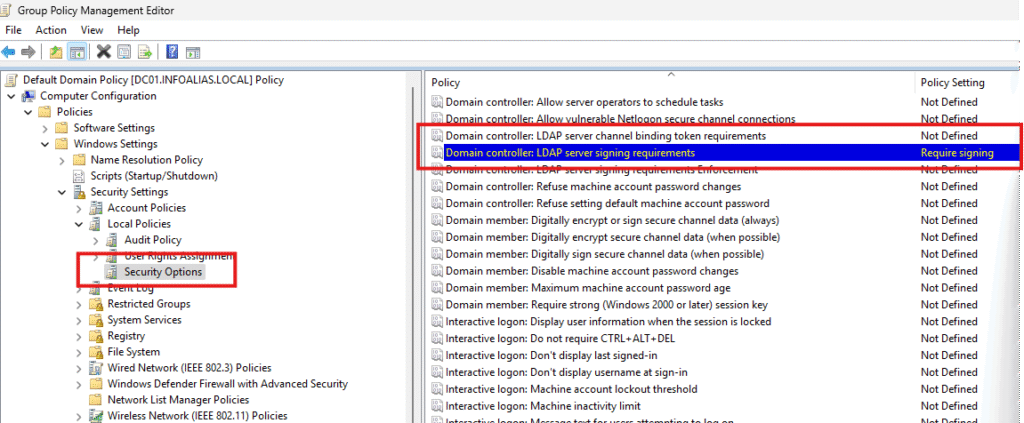
- Navigate to:
Computer Configuration → Policies → Security Settings → Security Options → Domain controller: LDAP Server Signing Requirements
4. Set “Domain controller: LDAP server signing requirements” to:
- Require signing
5. Apply and update policy:
gpupdate /force
6. Restart the DC.
This ensures clients must use LDAPS or LDAP with signing.
🔒 Option 2: Restrict Simple Binds via Registry
To block simple binds (unencrypted) entirely:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
Add or edit:
Value name: LDAPServerIntegrity
Value type: REG_DWORD
Value data: 2
- 0 = None (default, allows unsigned binds)
- 1 = Negotiate signing
- 2 = Require signing
Restart NTDS or reboot for the setting to take effect.
🧾 4. Enable LDAP Diagnostic Logging and Monitor Event IDs
Monitoring LDAP traffic helps verify secure communications and detect insecure binds. Windows provides LDAP interface events under the Directory Service logs.
🔧 Enable LDAP Logging
Use either Registry Editor or PowerShell to enable LDAP diagnostic logging.
Registry Method
Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics
Set the following DWORD values (1–5, where 5 is most verbose):
| Diagnostic Area | Key Name | Recommended Level |
|---|---|---|
| LDAP Interface Events | 16 LDAP Interface Events | 2 or higher |
| Internal Processing | 15 Internal Processing | 2 |
| Security Events | 2 Security Events | 2 |
Tip: Level
2is sufficient for identifying insecure LDAP binds without excessive logging.
After setting these, restart the NTDS service or reboot the domain controller.
📊 Important LDAP Event IDs
When LDAP diagnostic logging is enabled, monitor these event IDs under:
Event Viewer → Applications and Services Logs → Directory Service → LDAP Interface Events
| Event ID | Description | Meaning / Action |
|---|---|---|
| 2886 | The LDAP server is configured to allow simple binds or unsigned connections. | Warning: LDAPS not enforced. |
| 2887 | The LDAP server has processed unsecure (unsigned/simple) binds in the last 24 hours. | Indicates clients using insecure LDAP. |
| 2888 | An insecure LDAP bind was attempted. | Details about the client initiating it. |
| 2889 | The identity of a client using an insecure bind is logged. | Useful for identifying non-compliant systems. |
🧩 How to Use These Events:
- If you see 2887, insecure LDAP binds have occurred — check 2889 for source IPs and service accounts.
- Once you confirm all clients are LDAPS-compliant, enforce signing (
LDAPServerIntegrity=2).
🛡️ Best Practices
- Use Group Policy Autoenrollment to deploy certificates to all domain controllers.
- Regularly check certificate expiration dates.
- Update all apps and services to use ldaps://<FQDN>:636.
- Review LDAP events weekly to ensure compliance.
- Use Event Subscriptions or SIEM integration to alert on Event IDs 2886–2889.
✅ Conclusion
Securing LDAP traffic with LDAPS and enforcing signed connections significantly reduces the risk of credential theft or replay attacks. By combining LDAPS configuration, LDAP signing enforcement, and diagnostic event monitoring, you can maintain a hardened and auditable Active Directory environment.